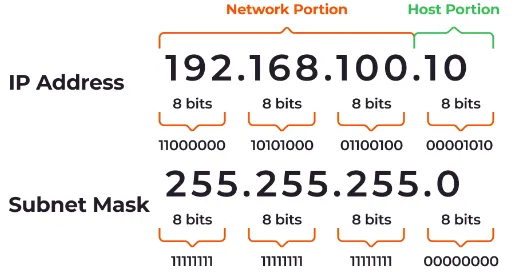
What you need to know about 2FA
Two-factor authentication (2FA) is the use of more than one way to verify a users identity on a computer system and allow access to an account.
Podcast @ Huon & Kingston FM
A discussion with Andy about how cyber security works and what we can do to protect ourselves
$700 000 Stolen from Grandfather in cyber attack
A grandfather had his mobile phone hacked with a keylogger. The criminals captured his username, password and pin for his banking app and then stole $700 000
How a Security Audit will stop you stepping in poo
Implementing a cyber protection solution it is important to understand the uniqueness of your business and the external requirements placed on your business.
Why Small Business Find it Hard to Implement Cyber Security (Part 1)
Five areas that are probably contributing to holding back small business from being cyber resilient and safe.
Cyber Bully and Harassment
Be aware of the possibility of cyber bulling and make sure you are protected.
A persistent criminal
Being aware and constantly alert to the possibility of cyber criminal activity is what protects
Security as a future IT function
What will future cyber security look like. What will be the responsibility of the business. What will services providers deliver
Is Apple macOS cyber safe
Apple has the feeling of being cyber safe. Is this still true 15 years after the launch of the iphone
What should be included in a cyber awareness program?
A cyber security training program needs to cater to the individual’s needs and activities.
How you can reduce employee stress and fight cyber crime
Not knowing how to be safe from cyber attacks is stressful. Implementing the right mitigation is important
Does building a cyber security human firewall need to involve complex training
How complicated does cyber security training need to be effective?
Is IT Support too busy to do cyber security training
Should you add cyber security awarness training as a responsibility of your IT support staff
What cyber security effort is most needed
Lifting the security profile is challenging. Using the aggregation of marginal gains allows organsations to be more compliant and cyber safe
The Perfect Human Firewall
Be perfect in setting up your cyber security program with one easy secret.
Why people are so important to cyber security
You cant rely on the IT department to have your back. You need to have the IT departments back in implementing cyber security.
What's in a policy
Your company policies are the laws that you set that keep your company safe. It is important to mindful of how they are constructed and the intention of each policy.
Australian Cyber Laws
Cyber crime is better fought when governments participate. Understanding the laws of your country related to cyber crime help you to know where to turn in the event of a crises.